How to Find and Fix a Backdoor in a Hacked WordPress Site
Has your WordPress website been hacked? Find and Fix a Backdoor in a Hacked WordPress Site.
Hackers often install backdoors to ensure they can get back into your website even after it’s secured. As long as you can get out of that back door, they are invincible.
In this article, we’ll show you how to find and fix a backdoor in a hacked WordPress site.

How to Tell if Your Website Has Been Hacked
If you run a WordPress website, you need to take security seriously. Because websites are attacked an average of 44 times per day.
You can learn best practices for keeping your site secure in our Best WordPress Security Guide.
But what if your site has already been hacked? Find and Fix a Backdoor in a Hacked WordPress Site
Some of the signs that your WordPress site has been hacked include low website traffic or performance, weak links or unknown file additions, a garbled home page, inability to log in, suspicious new user accounts, and more.
Cleaning up for a hacked website can be very incredibly painful and difficult. We walk you through the step-by-step process in our beginner’s guide to fixing your hacked WordPress site. Also, make sure hackers scan your site for any malware.
And don’t forget to remove the backdoor.
A smart hacker knows that you will clean your website eventually. What they can do is install a backdoor, so they can come back after you’ve secured the front door of your WordPress website.
What Is a Backdoor?
A backdoor is a code added to a website that allows a hacker to gain access to the server, leaving the rest undetected and bypassing normal logins. This allows a hacker to gain access to your website even after finding and removing an exploited plugin or vulnerability
The next step in the hack is to backdoor after the user logs in. You can learn about how WordPress sites get hacked and how to prevent it with our guide.
Backdoors often survive WordPress upgrades. This means that your site will remain unprotected until you fix every backdoor.
How Do Backdoors Work?
Some backdoors only hide admin usernames. They allow the hacker to log in, typically by typing in a username and password. Since the username is hidden, you don’t even know that someone else has accessed your website
A more complex backdoor could allow a hacker to execute PHP code. They manually send some of the hacking code to your website using their web browser.
Others have a full user interface that allows them to act as your WordPress hosting server for sending emails, running SQL database queries, and more.
Some hackers will leave multiple backdoor files. After uploading one, they will add another to confirm their access.
Where Are Backdoors Hidden?
In every case we found, the backdoor was disguised as a WordPress file. Backdoor code on a WordPress site is usually stored in the following locations:
- A WordPress theme, but probably not the one you’re currently using. The theme’s code isn’t overwritten when you update WordPress, so it’s a good place to put a backdoor. This is why we recommend removing all inactive themes
- WordPress plugins are another good place to hide backdoors. Like themes, they are not overwritten by WordPress updates and many users are reluctant to upgrade to plugins.
- The Uploads folder can contain hundreds or even thousands of media files, so it’s another good place to hide a backdoor. Bloggers almost never check its content because they just upload an image and then use it in the post.
- The wp-config.php file contains sensitive information that is used to configure WordPress. This is one of the most targeted files by hackers.
- The wp-includes folder contains the PHP files required for WordPress to run properly. This is another place where we get backdoors because most website owners don’t check what’s in the folder.
Examples of Backdoors We’ve Found
Here are some examples of backdoors that hackers have uploaded On one site we cleaned, the backdoor was in the wp-includes folder. The file was called wp-user.php, which looks innocent enough, but that file doesn’t actually exist in a typical WordPress installation.
In another example, we found a PHP file called hello.php in the uploads folder. It was disguised as a Hello Dolly plugin. The strange thing is that the hacker puts it in the uploads folder instead of the plugins folder.
We also found backdoors that do not use the .php file extension An example is a file called wp-content.old.tmp, and we’ve also found backdoors in files with a .zip extension.
As you can see, hackers can be very creative when it comes to hiding a backdoor.
In most cases, the files were encoded with base64 code that could perform all kinds of operations. For example, they can add spam links, add additional pages, redirect the original site to a spam page, and more.
That said, let’s see how to find and fix a backdoor in a hacked WordPress site.
How to Find a Backdoor in a Hacked WordPress Site and Fix It
Now you know what the back door is and where it might be hiding. The hard part is figuring it out! After that, it’s as simple as deleting the cleanup file or code.
1. Scan for Potentially Malicious Code
The easiest way to scan your website is with a WordPress Malware Scanner plugin. We recommend Securi because it helped us stop 450,000 WordPress attacks in 3 months, including 29,690 backdoor attacks.
They offer a free Sucuri security plugin for WordPress that allows you to scan your website for common threats and tighten your WordPress security. The paid version includes a server-side scanner that runs once a day and looks for backdoors and other security issues.
Learn more in our guide on how to scan your WordPress site for potentially malicious code.
2. Delete Your Plugins Folder
Searching through your plugin folders for suspicious files and code is time-consuming And since hackers are so sneaky, there’s no guarantee you’ll find a backdoor
What you can do is delete your plugins directory and then reinstall your plugins from scratch. This is the only way to ensure that there are no backdoors in your plugins
You can access your plugin directory using an FTP client or your WordPress host’s file manager. If you’ve never used FTP before, you might want to check out our guide on how to use FTP to upload files to WordPress.
You need to use software to navigate to your website’s wp-content folder. Once there, right-click on your plugins folder and select ‘Remove’.
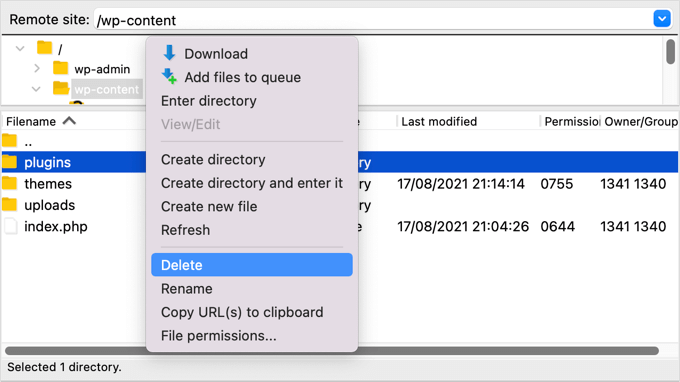
3. Delete Your Themes Folder
Likewise, it’s better to remove them than spend time searching for backdoors in your theme files.
After deleting your plugins folder, simply highlight the theme folder and delete the same.
You don’t know if there was a backdoor in the folder, but if it was there, it’s gone now. You’ve just saved time and you’ve removed an extra point of attack.
Now you can reinstall any theme you need.
4. Search the Uploads Folder for PHP Files
Next, you should take a look at the uploads folder and make sure there are no PHP files inside.
There is no good reason to have a PHP file in this folder as it is designed to store media files like images. If you find a PHP file there, it should be removed.
You’ll find the uploads folder in the wp-content folder, Like the plugins and themes folders. Inside the folder, you’ll find several folders for each year and month you uploaded your files. You need to check each folder for PHP files.
Some FTP clients offer tools that will search the folder repeatedly. For example, if you’re using FileZilla, you can right-click on the folder and select ‘Add file to queue’. Any files found in any subdirectory of the folder will be added to the row in the bottom pane.
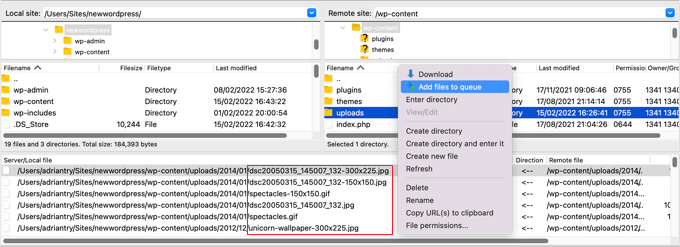
You can now scroll through the list looking for files with the .php extension.
Alternatively, advanced users who are familiar with SSH can write the following command:
| 1 | finduploads -name "*.php"-print |
5. Delete the .htaccess File
Some hackers can add redirect code to your .htaccess file that will redirect your visitors to other websites.
Using an FTP client or file manager, delete the file from your website’s root directory and it will be automatically recreated.
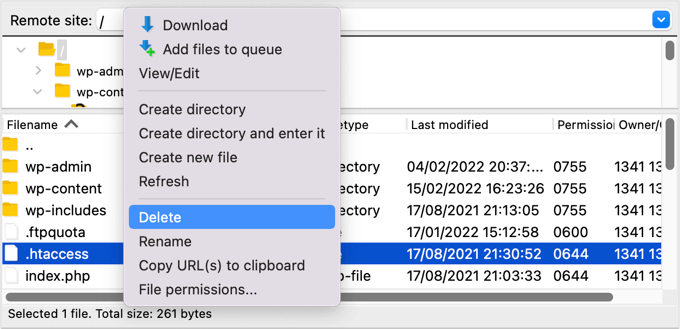
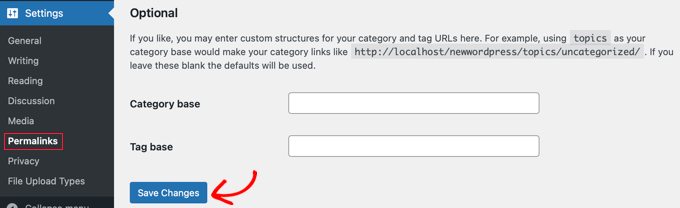
If for some reason it isn’t recreated, then you should go to Settings » Permalinks in your WordPress admin panel. Clicking the ‘Save Changes’ button will save a new .htaccess file.
6. Check the wp-config.php File
The wp-config.php file is a core WordPress file that contains information that allows WordPress to communicate with the database, security keys, and developer options for your WordPress installation.
The file is found in the root folder of your website. You can view the contents of the file by selecting the Open or Edit option in your FTP client.
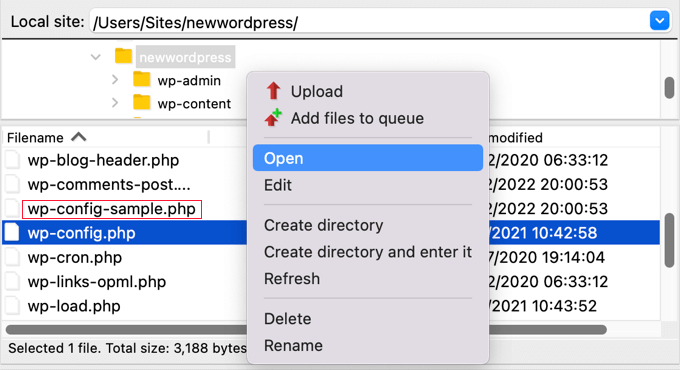
Now you should carefully check the contents of the file to see if there is anything. It may be helpful to compare the file with the default wp-config-sample.php file in the same folder.
You delete any code that you’re sure doesn’t belong.
7. Restore a Website Backup
If you are regularly backing up your website and are still worried that your website is not completely clean, restoring a backup is a good solution.
You should completely delete your website and then restore the backup taken before your website was hacked. This is not an option for everyone, but it will give you 100% confidence that your site is secure
For more information, see our beginner’s guide on how to restore WordPress from a backup.
How to Prevent Hacks in the Future?
Now that you’ve cleaned up your website, it’s time to improve your site’s security to avoid future hacks.
1. Regularly Backup Your Website
If you’re not already backing up your website regularly, today is the day to start.
WordPress does not come with a built-in backup solution. However, there are many great WordPress backup plugins that allow you to automatically back up and restore your WordPress website.
UpdraftPlus is one of the best WordPress backup plugins. It allows you to set up automatic backup schedules and will help you restore your WordPress site in case something bad happens.
Learn more in our guide to backing up and restoring your WordPress site with UpdraftPlus.

2. Install a Security Plugin
When you’re running your business, you probably won’t be able to monitor what’s happening on your website. So we recommend you use a security plugin like Sucuri.
We recommend Tsukuri because they are good at what they do. Major publications like CNN, USA Today, PC World, TechCrunch, The Next Web, and others agree with this. Also, we rely on it to keep Fixwebsoft safe.
3. Make WordPress Login More Secure
It is also important that you further secure your WordPress login. The best way to start is to enforce the use of strong passwords when users create accounts on your website. We recommend that you start using a password manager utility like 1Password
What you should do is add two-factor authentication. This will protect your website from stolen passwords and brute force attacks. This means that even if a hacker knows your username and password, they still won’t be able to log into your website.
Finally, you should limit login attempts in WordPress. WordPress allows users to enter passwords as many times as they want. Locking down a user after five failed login attempts will significantly reduce the chances of a hacker working on your login details.
4. Protect Your WordPress Admin Area
By protecting the admin area from unauthorized access you can prevent many common security threats. We have a long list of tips on how you can keep your WordPress admin secure.
For example, you can protect the password in the wp-admin directory. This adds another layer of security to your website’s most important entry point.
You can limit access to the admin area to IP addresses used by your team. This is another way to lock down hackers looking for your username and password.
5. Disable Theme and Plugin Editors
We that WordPress comes with a built-in theme & plugin editor? This plain text editor lets you edit your theme and plugin files directly from the WordPress dashboard.
While this is helpful, it can lead to potential security issues. For example, if a hacker gets into your WordPress admin area, they can use the built-in editor to gain access to all your WordPress data.
After that, they will be able to deliver malware or launch a DDoS attack from your WordPress website.
To improve WordPress security, we recommend removing the built-in file editors entirely.
6. Disable PHP Execution in Certain WordPress Folders
We know PHP scripts can be run in any folder on your website By default. You can further secure your website by disabling PHP execution in folders that are not needed
For example, WordPress is not required to run code stored in your uploads folder. If you disable PHP execution for that folder, a hacker won’t be able to run the backdoor, even if they successfully uploaded one there.
7. Keep Your Website Up to Date
Each new version of WordPress is more secure than the previous one. Whenever a security vulnerability is reported, the core WordPress team works diligently to release updates that fix the problem.
This means that if you do not keep WordPress up to date, you are using software with known security vulnerabilities. Hackers can discover websites running older versions and use vulnerabilities to gain access.
That’s why you should always update WordPress using the latest version of WordPress.
Don’t just keep WordPress up to date. You need to make sure that you keep your WordPress plugins and themes running as well.
We hope this tutorial helped you learn how to find and fix a backdoor in a hacked WordPress website. You may also want to learn more about moving WordPress from HTTP to HTTPS or our list of WordPress errors and how to fix them.
Suggest For You:







No comments